5 Steps You Should Take to Improve Mobile App Security
Written by Harini Krish
Lead Technical Content Writer
Mobile apps dominate this era, and in the last few years, mobile apps have taken over the world with changing consumer habits. Mobile apps and Smartphones have become an integral part of everyday life. Many companies have turned to mobile apps due to the increase in the number of smartphones and tablets worldwide.
Research shows that 90 percent of the time spent on mobile devices is spent on apps, more than mobile browsers. But we must keep in mind that “great opportunities come with great challenges.” The most challenging part of the Mobile app is its security and vulnerability.
The five important ways that can help you keep your app secure
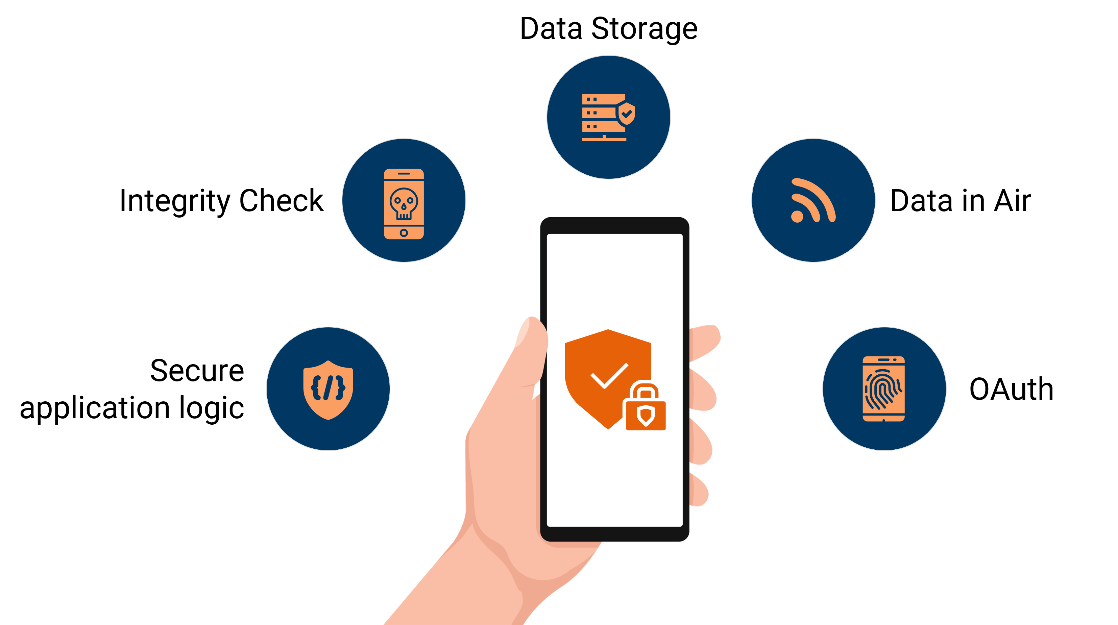
Data Storage
Most inexperienced developers do not understand the value of data storage security in a mobile app. Data Storage should accommodate all these validations, such as:
- Sensitive data should not be written on the application log.
- Sensitive data should not be shared with third parties unless it is a necessary part of the architecture.
- The keyboard cache should be disabled.
- Sensitive data should not be exposed through the IPC mechanism.
- Sensitive data such as pins or passwords should not be exposed during user interaction.
- Sensitive data should not be included in the backup generated by the mobile operating system.
- The user credential should be stored in the app through Key Chain / key store OR SQLChipher.
Data in Air
SSL pinning plays a significant role in building highly secure mobile apps. Data is used by many people across countless insecure wireless networks daily while using their mobile devices. Once ATS is enabled, the next step to increase security is to enable SSL Pinning. More security element is to be added to the mobile app. It uses certificate pinning to avoid man-in-the-middle attacks. When the public networks are used to communicate, it is vital to send and receive information securely.
OAuth
User Authentication and authorization are the new normal for all apps, be it B2C or B2B. Which is a must-have feature for the Mobile app as it gives more power to the owner of the app.
Integrity Check
Rooted devices are most vulnerable to attacks. The execution of an app on a rooted device should be avoided at all times. Mobile App should detect jailbroken phones by using libraries like Jail Monkey.
But it is also vital to understand that if you are targeting a larger audience, mainly B2C, you may lose business since these days, most mobile phones are rooted.
Secure application logic
Most of the developers are not aware of the Secure App Logic. Many developers do not even know about the fact that the build you create can be tempered with and debugged by reverse engineering of APK or IPA files. To avoid this, you can use a library such as; Jscrambler. This provides a series of layers that protect JavaScript and facilitates a Self-Defending layer that provides anti-debugging and anti-tampering capabilities.
A basic mobile application has raised million-dollar companies such as UBER, Instagram, Snapchat, and many more owe their existence to Mobile apps. For the same reason, you need to make sure that your million-dollar idea is secure. Royal Cyber has maintained its years of experience by developing secure apps for both customers and businesses. Connect with us today to get yourself a bulletproof app.



